Encrypting onchain data
Data uploaded to Irys is stored permanently on Arweave. Once on Arweave, this data becomes publicly accessible, anyone can view it. For projects where privacy is a concern, you can use LitProtocol (opens in a new tab) to encrypt your data before storing it on Irys.
This guide is an overview of what Lit Protocol is and how to use it with Irys. We also have code examples teaching how to do server-side and browser-based encryption. Additionally, the open-source Irys Provenance Toolkit has an encrypted uploader component (opens in a new tab) you can drop into any React-based project.
Lit Protocol
Lit Protocol enables developers to create and manage decentralized keys for condition-based encryption and programmatic signing for digital assets. In short, you can use it to:
- Encrypt data
- Define fine-grained access rules for who can decrypt data
- Decrypt data
Encrypted data can be stored on Irys, then retrieved and decrypted at any point in the future.
Irys + Lit use cases
Using Lit Protocol with Irys opens up new opportunities for builders, including:
- Gating access to content
- Encrypting posts for Lens protocol
- Decentralized identity verification
- Creating private data marketplaces
- Creating NFTs only viewable by their owner
- Storing private personal data on-chain
Using Lit Protocol, the access control conditions provide near infinite flexibility. Imagine a system for government bid management: bids are required to be submitted by a specific deadline, tracked using Irys' millisecond-accurate timestamps. The bids remain encrypted up to this deadline, aiding in preventing corruption by ensuring the bids are inaccessible to all parties until the designated time.
Encrypting data
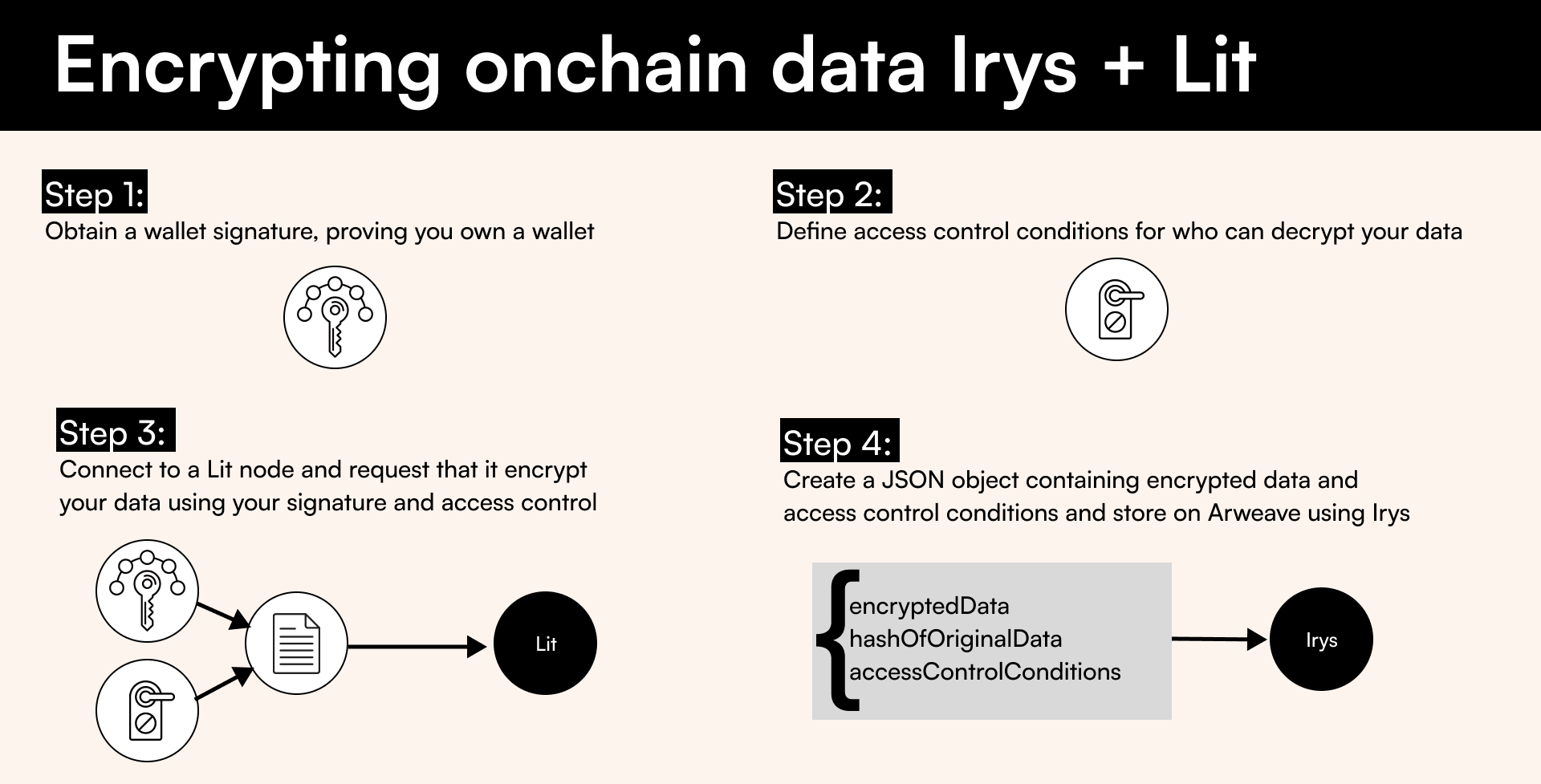
There are three steps to encrypting data
- Obtain a wallet signature (AuthSig (opens in a new tab)), which proves you own a wallet
- Define access control conditions (opens in a new tab) for who can decrypt your data
- Connect to a Lit node and request that it encrypt your data
Access control conditions
Lit Protocol enables users to set access control conditions (opens in a new tab) specifying who can decrypt data.
This provides builders with the flexibility to designate data decryption permissions, including:
- A single wallet address
- DAO membership
- Owners of an ERC20 or ERC721
- Outcomes from a smart contract call
- Outcomes from an API call
Decrypting data
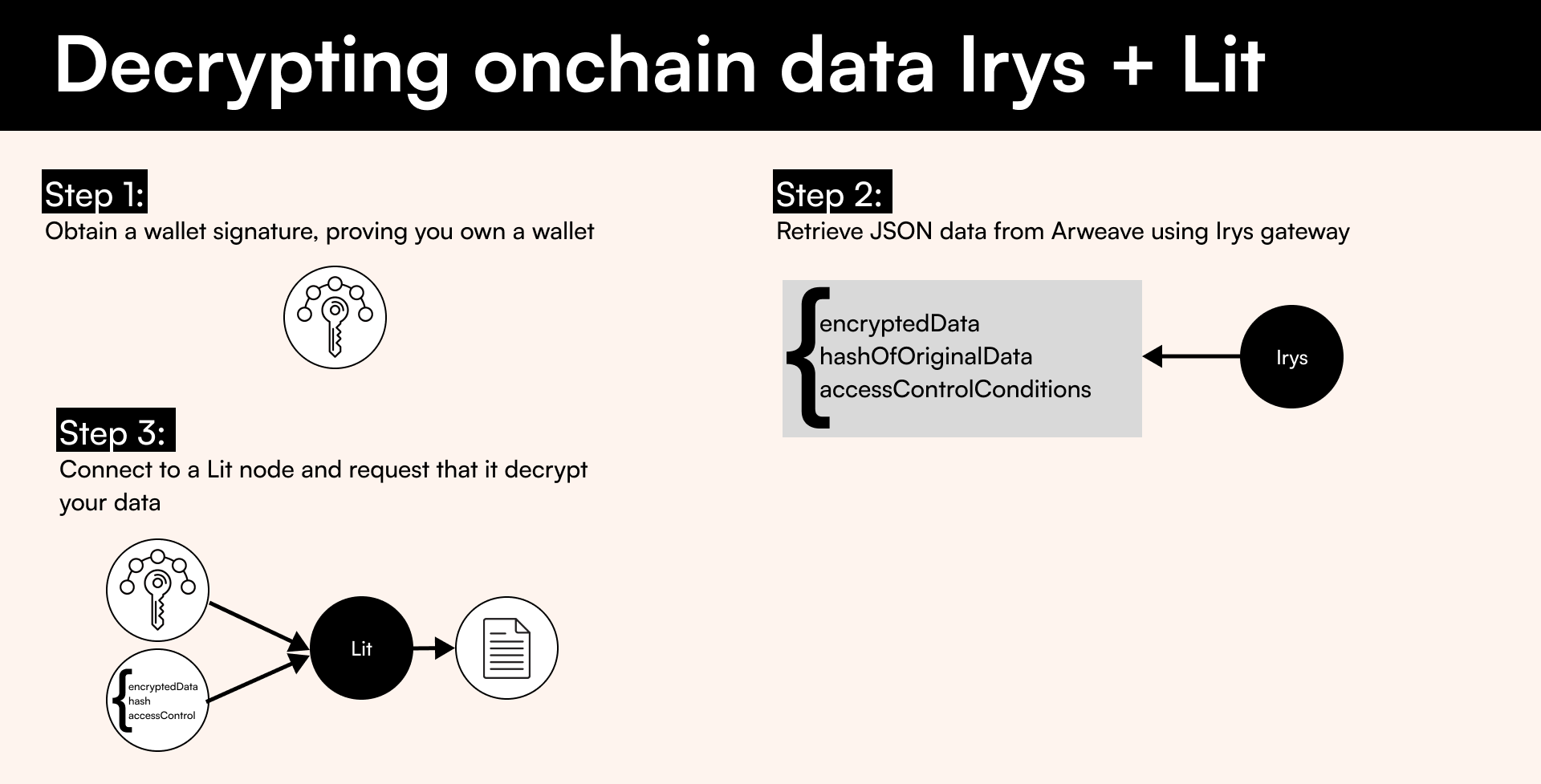
There are three steps to decrypting data:
- Obtain a wallet signature (AuthSig (opens in a new tab)), which proves you own a wallet
- Retrieve data stored on Arweave
- Connect to a Lit node and request that it decrypt your data